Unleashing the Power of Digital Internal Audit

Cyber threats are not new to humankind, especially for businesses. It is said that cyber-crime is the second largest crime in the world. It is calculated that every 39 seconds adds a hacker attack into the account. Isn’t it a scary fact? Yes, it is for sure. But still not sure why is this a significant issue? Let us find out why is it so?
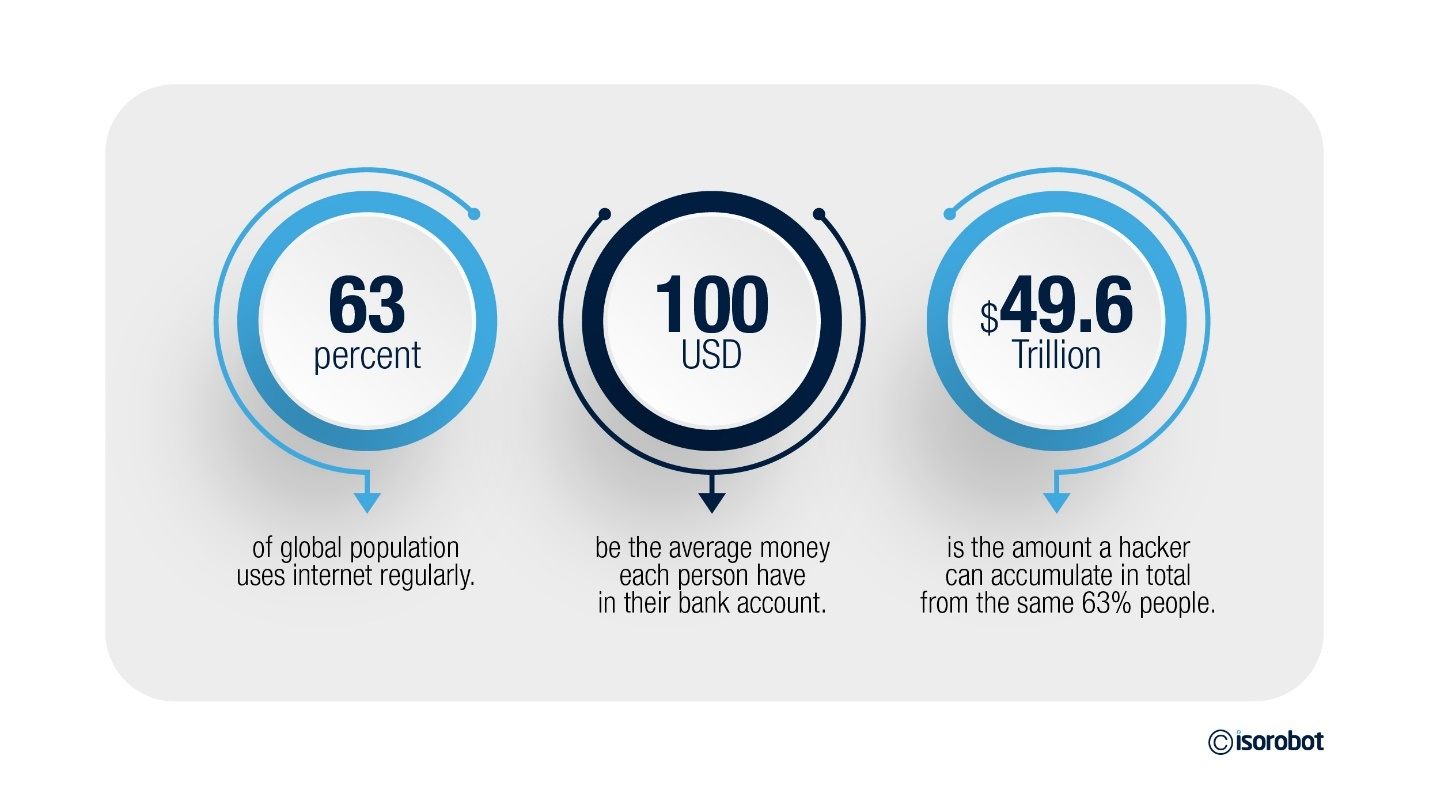
In this digital age, every person is connected to internet. According to the recent report from Statista.com, it is seen that 63% of the global population uses internet. Among them, about 4.65 billion people uses social media regularly. Now, taking the 63% of global population, let us assume everyone has $100 in their bank accounts. If it is so easy to hack your mobile or laptop you use for online transactions, then a single hacker can have $4,95,7,38,96,4413 from your data.
This is about the money, what if these hackers can have business information of leading global organisations that can even help hackers and intruders earn more than that was calculated. Even a single sheet of paper can cost millions of dollars. Your data can be held for ransom or sold on dark web marketplaces. Most enterprise risk management software can measure the impact of these crimes, but sometimes these ERMs need more advancements to prevent cybercrimes.
How can hackers get into our data privacy?
It is possible to steal your personal information with a variety of malware, such as keyloggers, info thieves, and banking malware. Login credentials, credit card information, browser autofill data, and cryptocurrency wallets are typically targeted by strains.
Cybercriminals use phishing to obtain sensitive information, such as login credentials, credit card information and personal identifiers, through low-tech social engineering techniques. Phishing attacks are usually circulated via email, also social media, text messages and phone calls.
Hackers can intrude into your online accounts if you leave your passwords open or without a secure password manager. This mostly includes bank application credentials, account details, credit card information, your contacts, social media accounts and other valuable data.
Online intruders can access your files easily using a public network where most people get connected. These networks could be unprotected as it is easily accessible to the public. Intruders can get into your systems using these networks connected to your systems.
OMG! How do hackers earn money from our data? What is the cost of data data that malicious hackers steal from us?
As discussed above, you will be now able to calculate the cost that hackers can earn by stealing your data. Not just the valuable data like credit card credentials and bank account details, but even simpler data are also priced in the underground economy that includes gaming platform accounts whose price range starts from $0.50 to $12, multimedia streaming accounts can earn the hacker from $0.1 up to $2, and cloud service & social media accounts prices from $5 to $50.
Now, calculating the amount of money a single person can help hackers from their gaming platform, multimedia platforms, cloud service accounts, medical notes and prescriptions can cost $100 on an average. This amount will be equal to 49.6 trillion in USD globally if cyber-attack occurs for all 63% of population, the same amount that we had discussed at the beginning.
If this is the situation of an individual, what is the impact of cyber-risk for an organisation?
An organisation is obviously a business with distinct types of documents, data, and credentials. For hackers, an organisation is a centralized hub to access all these data at the same time. Now, what data can be there in an organisation that hackers could steal for money? To reach the answer, we should investigate every aspect of business.
- Human Resources Information
An organisation must have a human resource department, to manage their workforce while onboarding, working, and relieving from the organisation. This can accumulate lot of data for an employee itself. This can include employment details, health information, salary details, work-related information, signature of the person, social security numbers, bank account information, educational details and much more. All these data can cost enough separately, or the hacker can demand ransom for this information.
- organisational Information
An organisation can have crucial documents that supports the smooth running of the business and is linked with their core business processes. This may include the company registration information, accreditation certificates, business documents, financial documents, asset information, blueprints, photographs, customer data, user passwords, server credentials, project details, business partner information and government certifications.
- Business Process Information
The organisation builds strategies every time a new trend or new requirement arises. Business process will always have loads of documents including plans, procedures, policies, internal audit reports, strategies, risk management plans and even trade secrets for companies who manufacture or provide unique products and services.
Financial information is the most vital and confidential data for any organisation.

Are there any effective ways to stay protected from cyber-crime?
The good news is, yes. There are many effective ways to create a protective shield against cyber-threats and crimes.
Introducing Cyber Security Management
This is the new cyber-security tool developed for business related cyber-risks. Information Security Management System (ISMS) is an enterprise-wide information protection system framework, which classifies information into need to know, good to know and need not to know categories. This is a part of cyber security system which protects information and data.
A cyber security system can build a resilient business and can give you the capability to fight against cyber-intruders who earn from the data of your arduous work. This is illicit to have your data by someone else as per the law. Protect your business and reduce your losses that comes as fine and loss.
However, cyber security management system software protects each of these information and helps organisations from exposing it to the internet criminals.
- Plan to prevent a data breach
It is always best to plan for the prevention and business continuity in response to a data breach if occurred. This can be circulating the adequate knowledge to oversee data effectively to ensure protection within the organisation. Efficient business continuity management system can help you manage these aspects easily.
- Keep your systems updated
Ensure that your system has a reliable and effective security system with anti-virus technologies. It is recommended to update security patches in regularly to prevent hacker attack. It is necessary to include DDoS enabled services for your systems.
It is always safe to have file back-ups and data back-ups regularly which will help you retain your valuable information at the point of cyber extortion. Again, with an ISMS it is easy to create back-ups on regular basis.
- Educate your workforce to recognize a threat
It is especially important to train your employees how to act against a cyber-threat, but particularly to identify them first. It is best to have a background check on employees to ensure their past. It is also a best practice to limit administrative capabilities for systems from employees. This can easily harm any business. These processes are part of a strong and smarter GRC software solution.
Modern businesses need modern and smarter solutions to be successful in the long run. It is reported that 95% of data breaches stolen records from the government, retail, and technology industries. Even in this day and age when everything is digital and with so much of technological advancements, we are not able to prevent this completely. This is not because we do not have solutions to bridle the cyber-attacks, but most businesses are not aware of the solutions already developed and protecting leading global companies. isorobot ISMS is such a smarter and capable solution that can help corporates, governments, SMEs, financial institutions, IT and ITeS firms and other industries who store bundles of information.
Discussing the benefits of ISMS solution makes the conclusion for this blog. It helps you win bids and gain customer trust by seamlessly managing multiple email chains, spreadsheets, and complex internal processes. Every bit of data is protected from third parties and unknown sources. All information security certificates are acquired, maintained, and managed by it. Moreover, it increases employee knowledge about best practices in information security while increasing resilience against cyberattacks. Information Security concerns are addressed while staying in compliance with international, national, statutory, and legal guidelines.
So, in simpler words, Information Security Management System is necessary for now and for the future, as cybercriminals realise the price of your data more than you. Grow resilient and stay safe from unwanted risks.